In the construction industry, managing the transportation of materials, equipment, and machinery to and from construction sites can be complex and challenging.
Let’s Connect!
Introduction
Challenges
A construction company had a large number of trailers, making it difficult to track their location and ensure their availability when needed.
Construction sites were vulnerable to theft and unauthorized access. It is crucial to monitor trailers and equipment to prevent losses and ensure site security.
Optimizing trailer utilization, coordinating deliveries, and minimizing delays are essential for efficient construction project management.
Challenges
Solution
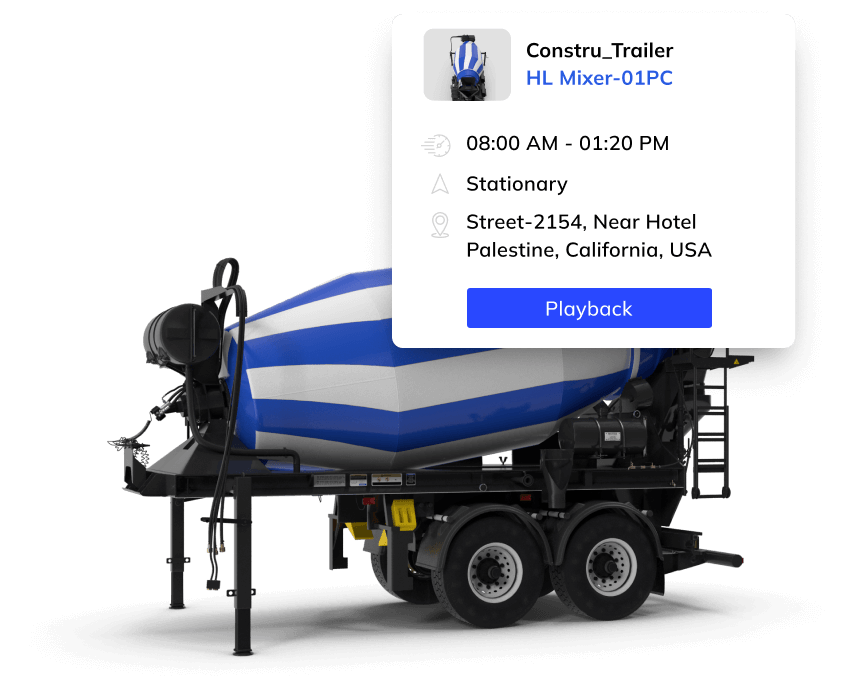
- Trailer tracking systems provided real-time visibility into the location and movement of trailers.
- Construction managers monitored trailers positions, ensuring they are dispatched to the right locations.
- Geofencing technology allowed construction companies to define virtual boundaries around construction sites.
- When a trailer equipped with a tracking device enters or exits these boundaries, alerts were triggered. This enabled proactive monitoring and enhanced security.
- By tracking trailer usage patterns, construction companies identifed underutilized trailers and optimize their allocation.
- This helps maximize equipment utilization, reduce idle time, and improve overall operational efficiency.
Results
- Enhanced Asset Management: Real-time tracking allows construction companies to locate trailers instantly, reducing the time spent searching for specific equipment. This improves asset management and minimizes downtime.
- Improved Security: Trailer tracking systems enhance security by providing alerts for unauthorized movement or theft attempts. Construction sites can quickly respond to such incidents, reducing the risk of equipment loss and unauthorized access.