700,000+ units | 50,000+ happy customers | 80+ countries
Fleet Management System
Product Description
Our advanced fleet management software significantly enables businesses to monitor their vehicles’ real-time location and movement. Additionally, they can oversee driver behavior to ensure safety and compliance while optimizing their fleet’s fuel usage.
Furthermore, it aids in reducing downtime by facilitating maintenance scheduling and tracking, which extends the vehicles’ lifespan.
In essence, our software transforms into a comprehensive solution for businesses aiming to streamline operations, enhance safety measures, and optimize resource utilization.
Moreover, whether it’s minimizing downtime through effective maintenance tracking or ensuring optimal fuel efficiency for each journey, our advanced fleet management software acts as a strategic partner in your business’s success.
Therefore, embrace the future of fleet management with a tool that doesn’t just monitor but actively contributes to the growth and sustainability of your fleet.
Features
Our software provides various features, such asfuel monitoring, tire management, video telematics, tire pressure monitoring, maintenance reminders, temperature monitoring, and monitoring of driving behavior, among others.
Furthermore, in addition to offering real-time insights, our software can efficiently automate tasks like dispatching, routing, and scheduling. It significantly minimizes the necessity for manual intervention.
One of the key features that sets our software apart is its ability to optimize fuel usage. Certainly, by providing detailed analytics and real-time data, businesses can make informed decisions to enhance fuel efficiency, undeniably leading to cost savings and reduced environmental impact.
This strategic approach aligns with modern sustainability goals, while positioning your fleet as a responsible and eco-friendly entity in the market.

Why choose our fleet management software?
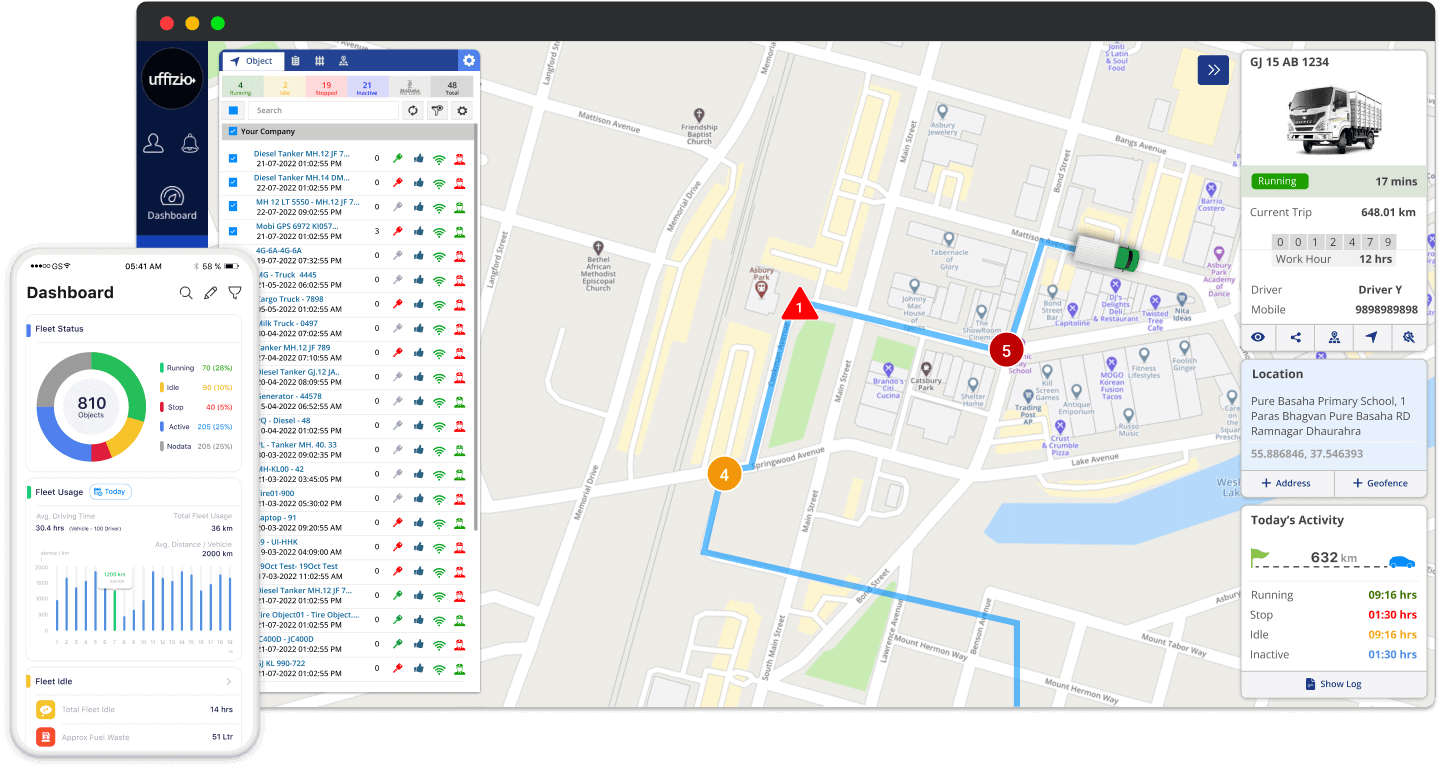
With our advanced vehicle tracking system you have complete control over your fleet and their activities.
Fuel Monitoring
Fuel monitoring system significantly provides valuable insights into fuel usage, drainage, and refilling. Fleet managers can easily access real-time data on fuel filling & drainage, along with other relevant information.
Tire Management
Surely, access both real-time and historical tire pressure data for your entire fleet. Additionally, you can set up alerts for extremely low tire pressures, helping you steer clear of unsafe driving conditions.
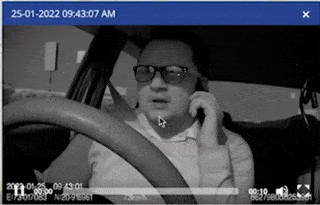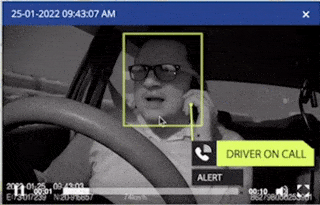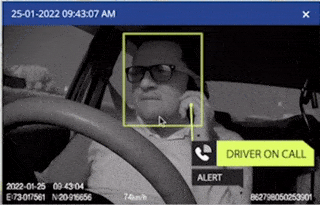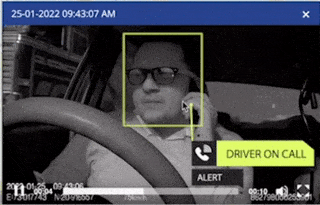
Video Telematics
Video telematics goes certainly beyond the capabilities of GPS tracking systems. Moreover, with our video monitoring solutions, you can experience the added benefits that set it apart from basic tracking.
Key Feature
Certainly, provide fleets with advanced tools to reduce workload and increase productivity.
Fleet Management Platform That Grows With You
Start with lite version and upgrade as you grow, or hit the ground running with one of our premium edition
- Complete Vehicle Analysis
Get insights into fleet travel time, distance, status, work hours, and GPS parameters.
- Alerts
- Fleet immobilization
The perfect anti-theft feature that allows you to disable vehicle ignition remotely.
- Geofence and Addresses
- Technician Module
Track everyday tasks. Get maintenance and installation analytics
- Multi-level user management
Create User hierarchies. Manage billing through flexible tariff plans.
- Available in multiple local & international languages
- Available as desktop and mobile applications
- Fuel Management System
- 35+ Alerts
- Temperature Monitoring
Real-time temperature drop or spike alerts to facilitate smooth cold chain logistics
- Engine Health Analysis
- Managing Expenses
- Maintenance Reminders
- RPM monitoring
Monitor RPM, work hours, and efficiency of your stationary equipment
- Sensor status & analytics
Compatible with analog and digital sensors
- Complete Driver Analysis
- Trakzee Driver App
A distinct app that your driver can use to track their daily trips
- Over 75 different alerts
- Video Telematics
ADAS and DMS Analysis with live-streaming & playback. Integrate AI dashams.
- Trip Planning & Classification
Assign stops or delivery points along the way. Get alerts for missed, delayed, upcoming stops. Also, classify trips into different categories like business or personal
- Tire Management
Real-time tire temperature and pressure analytics can be a lifesaver!
- Load Monitoring
Avoid overloading your trucks with an axle load monitoring system
- Elocks
- Ask for personal branding at an added cost
- Login Page Customization And theme selection
FAQ
Questions to ask before you invest
What is a fleet management system?
Certainly, A fleet management system provides real-time insights into your fleet. Moreover, it records and reports data trends that impact your fleet business, allowing you to make informed decisions. Additionally, with the assistance of a fleet management system, you can:
-
Enhance vehicle dispatch.
-
Automate trip routing for efficiency.
-
Manage engine health for optimal performance.
-
Monitor driver behaviors for safety.
-
Track operational costs for budget control.
-
Access estimated time of arrivals (ETAs) for better scheduling.
Can your fleet management support the size of my fleet?
Surely, our platform is versatile, and capable of accommodating anywhere from 10 to 1000 vehicles. Furthermore, you can tailor it to match your business’s size and nature effortlessly. Furthermore, it offers simple scalability options. This certainly allows you to adapt as your business requirements evolve. Undoubtedly use our software.
How can fleet management improve the safety of drivers?
Basically, Telematics can bring about notable safety enhancements for businesses in various industries. Thereby, it assists in identifying driver fatigue and unsafe driving, as well as addressing vehicle maintenance concerns. Moreover, by addressing these factors. It improves both driver and also vehicle safety
Is your fleet management reduce my insurance premiums?
Surely, Fleet insurance providers provide reduced premiums to fleets that have a clean accident record.
Additionally, you can qualify for discounted insurance rates when you integrate driver monitoring systems. Features such as dashcams and driver scorecards assist in identifying high-risk drivers.
Moreover, you can offer real-time coaching to ensure that drivers avoid reckless behavior. By proactively preventing aggressive driving, you can significantly enjoy savings on your insurance premiums.
Can I use Fleet Management software to reduce my fuel costs?
Surely, our Software facilitates real-time data exchange among sensors. Certainly, integrated fuel-level sensors work together with your fleet management platform to deliver valuable insights, including:
- Fuel depletion levels.
- Fuel replenishments.
- Vehicle distances traveled.
This significantly allows you to detect and deter fuel theft. Furthermore keeping track of your drivers’ idling habits and providing guidance for improved fuel efficiency.
How secure is your fleet management software?
Surely, Security is our top priority. Moreover, we employ advanced encryption and security measures to safeguard your data. Undoubtedly use our software for all your business needs.
What is route optimization, and how does it benefit fleets?
Basically, route optimization is the process of finding the most efficient routes for vehicles to minimize fuel consumption, reduce travel time, and improve overall productivity. Additionally, fleet management software with route optimization capabilities can help lower operating costs and improve customer service.